A. next-generation firewall security :
Prevent breaches automatically to keep the business moving
Are you protected 24/7? Our Solution constantly analyzes threat data and creates security protections that our Next-Generation Firewall uses to automatically prevent breaches. We stop attacks in their tracks so your business won’t miss a beat.
Visibility to detect and stop threats fast. Are you seeing the full picture? You can’t stop threats that you can’t see. Get the deepest network and security visibility using built-in advanced security features and advanced malware protection to detect and stop the most advanced threats fast.
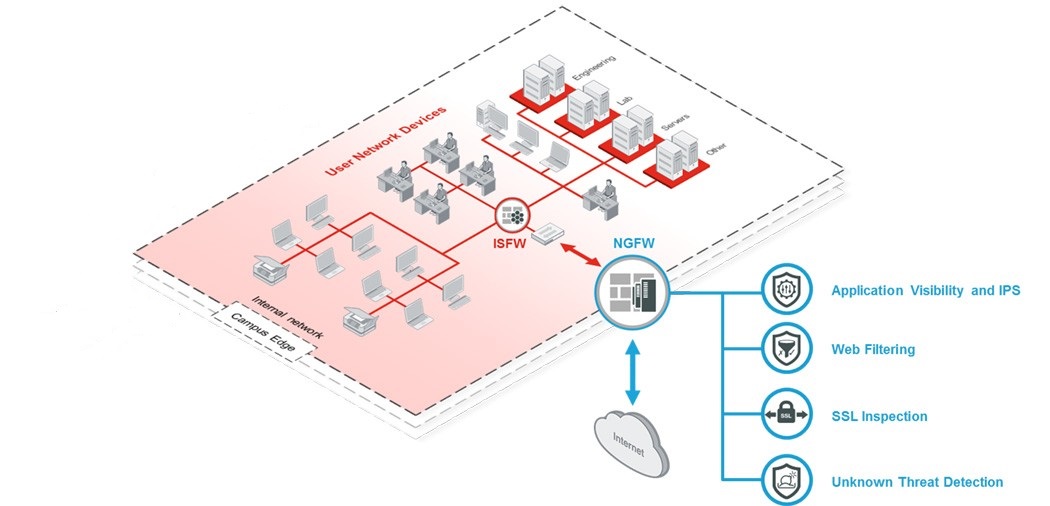
Automate operations to save time and reduce complexity. Stop playing whack-a-mole with threats. Let our Next-Generation Firewall do the work for you. Automated policy application and enforcement free up time so you can focus on high-priority tasks. Our firewalls work with the rest of our integrated security tools to see and stop threats faster.
B – Network Access Control – NAC:
IoT and BYOD increase access points and vulnerabilities in your network. Network Access Control solutions provide you the visibility and control you need. Develop, implement, and enforce security policies for controlling device and user access. Identify and stop threats based on security polices from mobile devices as they attempt to access your network. HBC IT provide a comprehensive and easy-to-deploy endpoint assessment and network access control (NAC) solution, NAC Advanced controls access to the network for guest, unmanaged and unauthorized computers. Non-compliant computers are identified and isolated, based on a centrally defined, policy driven assessment.
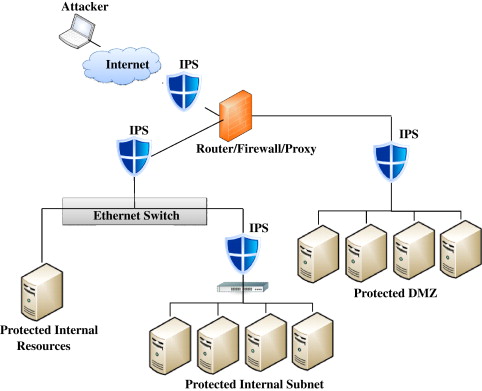
C -Intrusion Prevention Systems:
Protect against the full range of threats in your network Only complete visibility into all network traffic and activity will keep your network security ahead of targeted attacks that bypass traditional controls, exploit network vulnerabilities, and ransom or steal sensitive data, communications, and intellectual property.
We provide best-of-breed intrusion prevention to protect against the full range of threats at wire speed anywhere on your network to protect your critical data and reputation.
Real-time security: Get proven network reliability and availability through automated, in-line inspection without impeding network performance
Threat intelligence: Achieve protection from advanced threats through industry-leading global threat intelligence
Centralized insight: Integrate and prioritize security policy, response, and visibility with centralized management
Machine learning: Maximize real-time protection with patented machine learning techniques.
D- Network Traffic Analysis – NTA
Our network traffic analyzer have the following key features which is important for security operations with an emphasis on enterprise security:
Real-time network data analysis – To provide accurate detection, investigation, and response capabilities within a timeframe where they’re actually usable, every NTA product needs to conduct analytics and deliver answers in real time, at scale.
Complete east-west transaction visibility – For a network traffic analyzer to provide high-fidelity insight into threat behaviors, it needs to be able to see and analyze the actual contents of the network conversations.
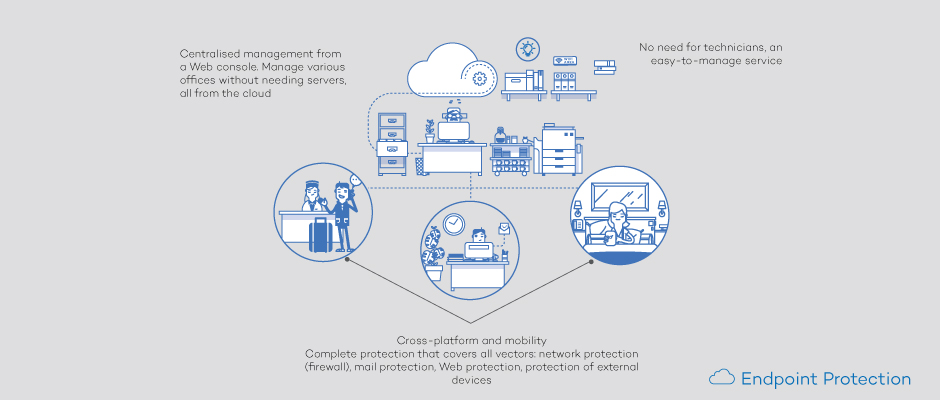
E – Endpoint Protection& Response:
Today, corporate endpoints represent one of the top areas of security risk for organizations. As malicious actors increasingly design their attacks to evade traditional endpoint prevention and protection tools, organizations are looking to endpoint detection and response (EDR) for additional visibility, including evidence of attacks that might not trigger prevention rules.
Antivirus -Our End Point Protection Solution is a Centralized management Solution itcan be deployed on premises or in the cloud. It provides greater visibility, simplifies operations, boosts IT productivity, unifies security, and reduces costs.
Advanced anti-malware protection: Our anti-malware engine is continually updated by our Global Threat Intelligence and works efficiently across multiple operating systems.
Machine learning analysis:Detect zero-day threats in near real time by examining how they look and behave to halt threats designed to evade detection.
Ransomware/ Greyware:Dynamic application containment: Defend against ransomware and greyware by securing endpoints that are leveraged as entry points for attacks.
Proactive web security: Ensure safe browsing with web protection and filtering for endpoints.
Actionable threat forensics:Quickly see where infections are, why they are occurring, and the length of exposure to understand the threat and react more quickly.